Keeping it confidential
SUAVE computors have two modes of operation: regular and confidential (sometimes called off-chain).
Regular mode is the same as the normal EVM. Confidential mode uses the MEVM, with its additional APIs, and the precompiles available in builder solidity, to ensure that transaction data provided by users remains private until executed on their blockchain of choice.
Builder solidity uses (and extends) all the tools and patterns you know and love. However, the concept of confidential computation being done off-chain by specific SUAVE computors is new and worth emphasizing.
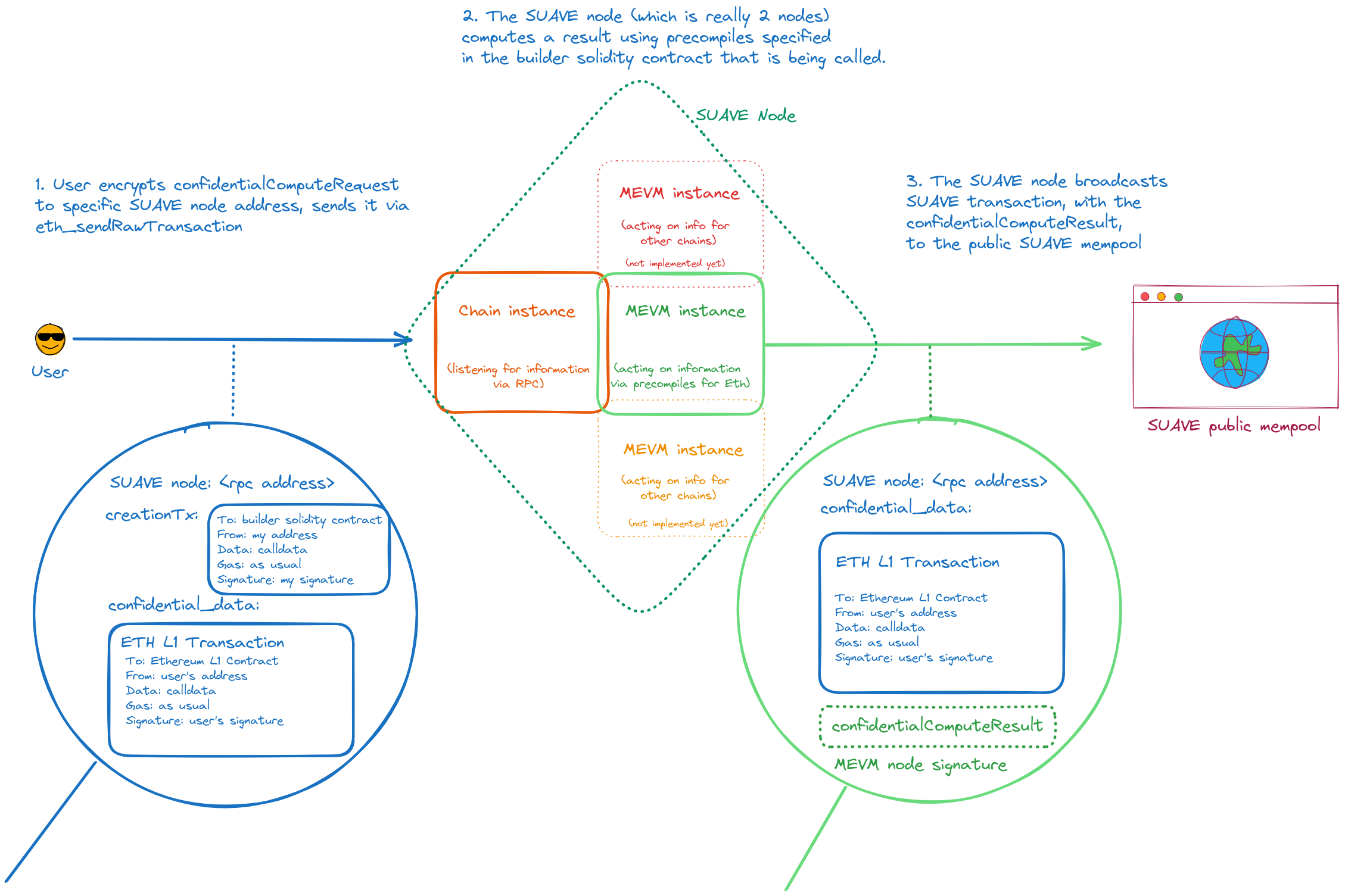
Users can encrypt their transaction data for specific SUAVE computors. Those nodes run the necessary computation (as defined in the public contract referenced in the transaction data), and insert the result into the calldata of a SUAVE transaction that is submitted to the public mempool, ensuring that only the results (and not the input) are broadcast publicly.
This is the way we combine the benefits of public, verifiable mechanisms with private data.
Flow
You can sign and submit transactions as you ordinarily would on Ethereum and they will work as expected.
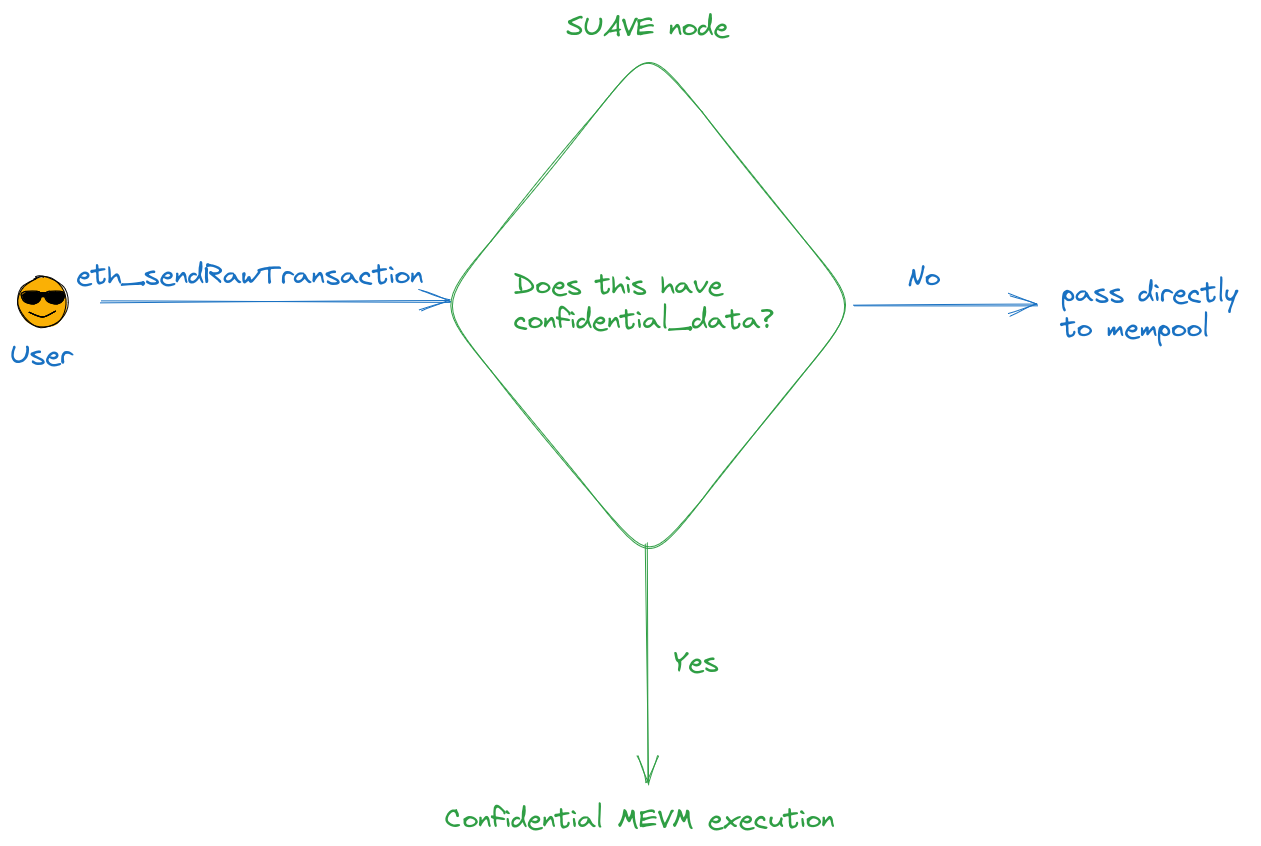
We describe here what occurs when you want your transaction data to remain confidential.
- Create a
confidentialComputeRequestand specify a SUAVE computor: i.e. an address whose signature over the confidential computation result will be trusted. - The MEVM instance executes the transaction in confidential mode, creating a
confidentialComputeResult. - The
confidentialComputeResultis set as the calldata in a "SUAVE transaction", which is broadcast to the public mempool. - We call this a "SUAVE transaction" because it is a normal EVM transaction, with an extra check to make sure that the SUAVE computor's signature matches the requested SUAVE computor in (1)
Please take a look through our how to write builder solidity guide if you want to dive deeper into the specifics of how each step occurs.
Key terms
For clarity, let's define confidentialComputeRequest and confidentialComputeResult, as well as introduce the idea of a confidentialDataStore.
confidentialComputeRequest
confidentialComputeRequestis a request for confidential computation, encrypted to a specfic (set of) SUAVE computor(s).- The "hint", which is some (or all) of an ordinary Ethereum transaction, is set as a "confidential input".
- It specifies the address(es) of the SUAVE computor for whom the data in the transaction is encrypted.
- A
creationTx, which specifies the builder solidity contract that holds the logic which the MEVM instance on the specified SUAVE computor must execute. - The request is sent via
eth_sendRawTransactionand is not necessarily sent directly to the mempool.- Before nodes broadcast
RawTransactionsthey receive, they check if there are confidential inputs. - If there are none, the node broadcasts the transaction directly to the public SUAVE mempool, operating in "regular" mode.
- If there are confidential inputs present, the SUAVE computor enters "confidential" mode, which uses the MEVM.
- Before nodes broadcast
confidentialComputeResult
confidentialComputeResultis the result of the confidential computation, shared with the whole SUAVE chain.- Upon receiving a
confidentialComputeRequest, the MEVM will enter into the builder solidity contract specified in thecreationTx. - This contract will use a precompile like
fetchConfidentalInputsthat enables the MEVM to fetch data encrypted for it, with which it computes a result. - This
confidentialComputeResultis placed alongside theconfidentialComputeRequestinitially received, and sent to the mempool.- This is all happening in a view function, and we don't want to expose the confidential inputs.
- So, this result is really a callback to another function which does permute state, the inputs for which are stored on the SUAVE computor in question, in its
confidentialDataStore.
- Therefore, confidential execution is not verifiable during on-chain state transition. However, we check that the signature of the SUAVE computor on a SUAVE transaction comes from the public address for which the original request was encrypted.
- State transition only depends on the result of the callback in the
confidentialComputeResult, so it remains fully reproducible. - SUAVE transactions are propagated through the mempool and inserted into blocks as expected, unifying confidential operation with regular operation.
- Upon receiving a
confidentialDataStore
confidentialDataStoreis an offchain data store. Builder solidity contracts tell the MEVM where to store particular information, such that the MEVM can access information other functions (or other contracts) need without storing it in the contract on chain and thereby exposing it to everyone.- Builder solidity contracts tell the MEVM to store data relevant to its operation in specific "keyspaces".
- This is done locally, on the specific SUAVE computor for whom the
confidentialComputeRequestwas encrypted. - It's best to look directly at our how to write builder solidity guide to get a deeper intutition for how this happens.
Pictures
FAQs
1. How do we ensure that a confidentialComputeRequest reaches its intended SUAVE computor(s)?
2. How do SUAVE computors get paid for confidential execution, or how do we protect against spam?
confidentialComputeRequest. These requests also include a creationTx with a gas price, thereby limiting spam. How to price SUAVE gas correctly without leaking too much information about the nature of the request is an active area of research.